Introduction to firewall principles The firewall can enhance the security of the organization's internal network. The firewall system determines which internal services can be accessed by the outside world; who can access the internal services and which external services can be accessed by internal personnel. The firewall must only allow authorized data to pass through, and the firewall itself must be able to avoid penetration. Disadvantages Proxy firewall Second generation: dynamic packet filtering 2. Proxy firewall Second generation: dynamic packet filtering 2. Proxy firewall Second generation: dynamic packet filtering 2. Proxy firewall The most prominent advantage of proxy-type firewalls is security. Because each connection between the internal and external networks must be intervened and converted by the Proxy, processed by a secure application program specifically written for specific services such as Http, and then the firewall itself submits requests and replies, not for internal and external networks. The computer has the opportunity of any direct conversation, thus preventing the intruder from using a data-driven type of attack to invade the internal network. It is difficult for a packet filtering type firewall to completely avoid this loophole. Just like you are going to submit a statement to a strange and important person, if you give this statement to your lawyer first, then the lawyer will review your statement and confirm that there is no negative impact before it is handed over by him The stranger. During this period, the stranger knows nothing about your existence. If you want to invade you, he will face your lawyer, and your lawyer will certainly know more about how to deal with this kind of person than you. The biggest disadvantage of proxy firewalls is that the speed is relatively slow. When users have relatively high throughput requirements for internal and external network gateways (for example, when they require 75-100Mbps), proxy firewalls will become a bottleneck between internal and external networks. Fortunately, the speed at which users currently access the Internet is generally much lower than this number. In the real environment, it is necessary to consider the use of packet filtering firewalls to meet the speed requirements. Most of them are firewalls between high-speed networks (ATM or Gigabit Ethernet, etc.). There is a control channel between the adaptive agent and the dynamic packet filter. When configuring the firewall, users only need to set the required service type, security level and other information through the corresponding proxy management interface. Then, the adaptive proxy can decide whether to use the proxy service to request from the application layer proxy or forward the packet from the network layer based on the user's configuration information. If it is the latter, it will dynamically notify the packet filter to increase or decrease the filtering rules to meet the dual requirements of users for speed and security. Second and third generation firewalls
USB LED Desk Lamp
360°all-direction illumination and touch the switch to adjust lightness of the lamp
Features And Functions of the USB LED desk lamp:
USB LED Desk Lamp USB LED Desk Lamp,Portable USB LED Desk Lamp,Fashionable USB LED Desk Table,Modern USB LED Desk Lamp Shenzhen Superlight Technology Co., Ltd. , https://www.superlighttech.com
Five functions of firewall
Generally speaking, the firewall has the following functions:
1. Allow network administrators to define a central point to prevent illegal users from entering the internal network.
2. Can easily monitor the security of the network and alarm.
3. It can be used as a place to deploy NAT (Network Address TranslaTIon), using NAT technology to dynamically or statically associate a limited IP address with an internal IP address to alleviate the shortage of address space.
4. It is the best place to audit and record Internet usage fees. Here, the network administrator can provide the cost of Internet connection to the management department, find out the location of potential bandwidth bottlenecks, and can provide department-level billing based on the institution's accounting model.
Comparison of two firewall technologies
Packet filtering firewall
advantage
Lower price
Low performance overhead and fast processing speed
Complex definition, prone to problems caused by improper configuration
Allow data packets to pass directly, easily causing the potential danger of data-driven attacks
Built-in Proxy application specially designed to improve security, can thoroughly understand the commands of related services, and securely process incoming and outgoing data packets
The speed is slow, so it is not suitable for applications between high-speed networks (ATM or Gigabit Ethernet, etc.)
5. It can be connected to a separate network segment, physically separated from the internal network segment, and a WWW server and FTP server are deployed here as a place to publish internal information to the outside. From a technical point of view, it is the so-called ceasefire zone (DMZ).
Two major categories of firewalls
Although the development of the firewall has gone through the above-mentioned generations, according to the processing method of the internal and external data of the firewall, the firewall can be roughly divided into two major systems: packet filtering firewall and proxy firewall (application layer gateway firewall). The former is represented by Israel ’s Checkpoint firewall and Cisco ’s PIX firewall, while the latter is represented by the US NAI ’s Gauntlet firewall.
1. Packet filtering?
The first generation: static packet filtering
This type of firewall examines each packet according to defined filtering rules to determine whether it matches a certain packet filtering rule. The filtering rules are formulated based on the header information of the data packet. The header information includes IP source address, IP destination address, transmission protocol (TCP, UDP, ICMP, etc.), TCP / UDP destination port, ICMP message type, etc. A basic principle to be followed by a packet filtering type firewall is the "least privilege principle", that is, those packets that the administrator wishes to pass are explicitly allowed, and other packets are prohibited. 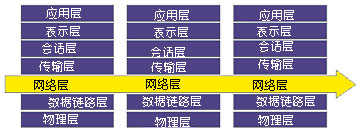
Figure 1 Simple packet filtering firewall
This type of firewall uses the method of dynamically setting packet filtering rules to avoid the problems of static packet filtering. This technology later developed into so-called packet state monitoring (Stateful InspecTIon) technology. The firewall adopting this technology keeps track of every connection established through it, and can dynamically increase or be more green in the filtering rules as needed? 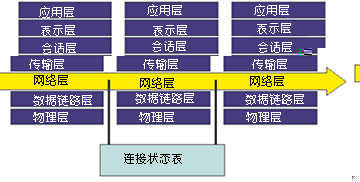
Figure 2 Dynamic packet filtering firewall
First generation: proxy firewall
The proxy firewall is also called the Application Layer Gateway (ApplicaTIon Gateway) firewall. This firewall participates in the whole process of a TCP connection through a proxy technology. After the data packets sent from the inside are processed by such a firewall, it is as if it originated from the external network card of the firewall, so as to hide the internal network structure. This type of firewall is recognized by network security experts and the media as the most secure firewall. Its core technology is the proxy server technology.
The so-called proxy server refers to a program that processes connection requests on the server on behalf of the client. When proxy servers get a client ’s connection intent, they will verify the client ’s request and process the connection request through a specific secure Proxy application, pass the processed request to the real server, and then accept the server response and do After further processing, the response is handed over to the requesting end customer. The proxy server plays a role of intermediate transfer when the external network applies for services to the internal network.
This type of firewall uses the method of dynamically setting packet filtering rules to avoid the problems of static packet filtering. This technology later developed into so-called packet state monitoring (Stateful InspecTIon) technology. The firewall adopting this technology keeps track of every connection established through it, and can dynamically increase or be more green in the filtering rules as needed? 
Figure 2 Dynamic packet filtering firewall
First generation: proxy firewall
The proxy firewall is also called an application gateway firewall. This firewall participates in the whole process of a TCP connection through a proxy technology. After the data packets sent from the inside are processed by such a firewall, it is as if it originated from the external network card of the firewall, so as to hide the internal network structure. This type of firewall is recognized by network security experts and the media as the most secure firewall. Its core technology is the proxy server technology.
The so-called proxy server refers to a program that processes connection requests on the server on behalf of the client. When proxy servers get a client ’s connection intent, they will verify the client ’s request and process the connection request through a specific secure Proxy application, pass the processed request to the real server, and then accept the server response and do After further processing, the response is handed over to the requesting end customer. The proxy server plays a role of intermediate transfer when the external network applies for services to the internal network.
This type of firewall uses the method of dynamically setting packet filtering rules to avoid the problems of static packet filtering. This technology later developed into the so-called Stateful Inspection (Stateful Inspection) technology. The firewall adopting this technology keeps track of every connection established through it, and can dynamically increase or be more green in the filtering rules as needed? 
Figure 2 Dynamic packet filtering firewall
First generation: proxy firewall
The proxy firewall is also called an application gateway firewall. This firewall participates in the whole process of a TCP connection through a proxy technology. After the data packets sent from the inside are processed by such a firewall, it is as if it originated from the external network card of the firewall, so as to hide the internal network structure. This type of firewall is recognized by network security experts and the media as the most secure firewall. Its core technology is the proxy server technology.
The so-called proxy server refers to a program that processes connection requests on the server on behalf of the client. When proxy servers get a client ’s connection intent, they will verify the client ’s request and process the connection request through a specific secure Proxy application, pass the processed request to the real server, and then accept the server response and do After further processing, the response is handed over to the requesting end customer. The proxy server plays a role of intermediate transfer when the external network applies for services to the internal network. 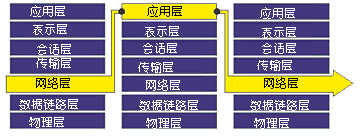
Figure 3 Traditional proxy firewall
Second generation: adaptive proxy firewall
Adaptive proxy technology (Adaptive proxy) is a revolutionary technology recently implemented in commercial application firewalls. It can combine the advantages of the security of the proxy firewall and the high speed of the packet filtering firewall to increase the performance of the proxy firewall by more than 10 times on the basis of no loss of security. There are two basic elements that make up this type of firewall: Adaptive Proxy Server (Adaptive Proxy Server) and Dynamic Packet Filter (Dynamic Packet filter). 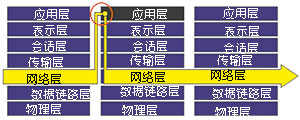
Figure 4 Adaptive proxy firewall
Small information
The history of firewall development
First generation firewall
The first-generation firewall technology appeared almost at the same time as the router, and adopted packet filter technology. The following diagram shows the simple development history of firewall technology. 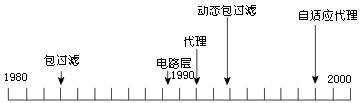
In 1989, Dave Presotto and Howard Trickey of Bell Labs launched the second-generation firewall, the circuit-layer firewall, and at the same time proposed the preliminary structure of the third-generation firewall, the application layer firewall (proxy firewall).
Fourth generation firewall
In 1992, Bob Braden of the USC School of Information Science developed the fourth generation firewall based on Dynamic packet filter technology, which later evolved into the so-called Stateful inspection technology. In 1994, the Israeli company CheckPoint developed the first commercialized product using this technology.
Fifth generation firewall
In 1998, NAI introduced an adaptive proxy technology, which was implemented in its product Gauntlet Firewall for NT, which gave a brand-new meaning to the proxy-type firewall, which can be called the fifth-generation firewall.
Energy Efficient LED Desk Lamp that will reduce energy spending by 75%
Desk Lamp that is pleasant on the eyes with flicker-free lighting for reading, working, and studying
1. High tech: modern surface light-emiting: stable and soft.
2. Lighting features: close to natural light: brightness; flicker free; eye protection.
3. High quality led chips: 50000 hours warranty of lighting lifespan.
4. Fashional design: adjustable beans;easy for delivery.
5. Functions: CCT adjustable and USB functions;
6. Important material: use roughly 4mm thickness led guide plate,to ensure that the light distribution more evenly, better for the eyes.
7. Lamp options: different color for selection; neautral or customized color packaging;logo and label print.
8. Environmentally friendly: energy-saving;green materials.