To use these connectors, the ribbon cable is inserted into the Ribbon Connector and the connector is then plugged into the Ribbon Connector on the circuit board. The connectors are designed to provide a secure and reliable connection that can withstand repeated insertions and removals. 2.54Mm Ribbon Connector,Pressure Welding Bar Connector,Pressure Welding Bar Connectors,Welding Bar Connector YUEQING WEIMAI ELECTRONICS CO.,LTD , https://www.wmconnector.com
Overall, the 2.54mm Ribbon Connectors are an essential component in many electronic devices that require a reliable and secure connection between the ribbon cable and the circuit board.
Is face recognition really safe? iPhoneX as an example to explain the data threat problem
The iPhone X’s face recognition technology has sparked a wave of enthusiasm, making facial unlocking a trend. As we enjoy the convenience of being able to unlock our devices with just a glance, have we ever paused to consider whether this technology is truly secure and if our personal data is protected at the highest level?
What kind of data security concerns does the iPhone X's facial recognition raise?

At Apple’s recent conference, the iPhone X captured everyone’s attention, not only for its sleek design but also for its groundbreaking features like Face ID, dual cameras, and augmented reality. The device was hailed as “defining the future of smartphone form,†marking a new era in mobile technology while paying tribute to Steve Jobs, the visionary behind the original iPhone.
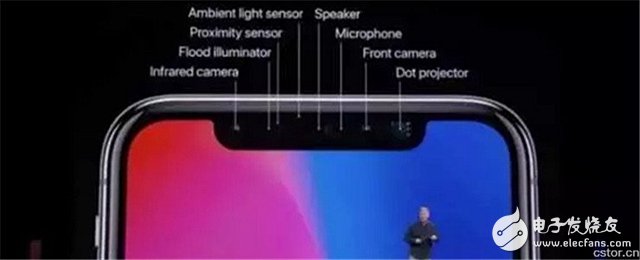
**How does 3D face unlocking become a reality?**
Face ID is undoubtedly one of the iPhone X’s most impressive features. During the launch, Apple highlighted nine key aspects: face verification, depth sensing, simple registration, specialized neural network, security, natural interaction, user privacy, attention-aware, adaptability, and integration with Apple Pay. Tim Cook emphasized the security of Face ID, stating that the chance of someone else unlocking your phone is about one in a million—far more secure than Touch ID.
This is made possible by the hidden "front-facing tech": four of the eight components are involved in facial recognition, including an infrared camera, floodlight, ambient light sensor, and dot matrix projector. These work together to capture 30,000 sampling points, creating a 3D map of the user's face. Every time you unlock your phone, the system compares the latest data with the stored information and processes it through the A11 chip’s Neural Engine.
While Face ID has amazed users, it has also raised serious concerns about personal privacy and data security. Netizens have expressed their worries with humor and skepticism:
Senator Al Franken from Minnesota even questioned Apple about potential misuse of facial data, urging the company to be transparent about how it stores and protects biometric information. Meanwhile, research from Stanford University showed that deep learning models can accurately predict sexual orientation based on facial features, sparking public debate over the ethical implications of such technologies.
Our analysis using the Qingbo big data public opinion monitoring system found that 12.43% of netizens expressed negative emotions about the privacy risks associated with the iPhone X, while 29.5% were neutral—indicating widespread concern.
**Face recognition isn’t just for iPhones**
Face recognition isn’t exclusive to the iPhone X. Before its release, Samsung and Xiaomi had already introduced similar features, though they relied on 2D imaging, which made them vulnerable to attacks using photos or masks. This led to criticism and highlighted the need for more advanced systems.
Today, face recognition is being adopted across various industries—from access control systems and surveillance to payments and travel. In China, for example, Wuhan Railway Station launched facial recognition for ticketing, and Alipay introduced face payment for commercial use. More and more sectors are integrating this technology into daily life, signaling the dawn of a “face-based†era.
**Does face recognition sell personal information?**
Apple claims Face ID is 20 times more secure than Touch ID, thanks to its 3D structured light technology, which creates detailed depth maps that resist fake attempts. However, global data breaches show that information security remains a pressing issue. In 2016 alone, there were over 900 data leaks worldwide, with financial theft and account hacking being the most common types.
In China, the Xu Yuyu case became a national tragedy, highlighting the dangers of telecom fraud. With increasing cases of identity theft and spam calls, many people are worried about the safety of their personal data.
Moreover, internet companies collect vast amounts of user data to create personalized ads, raising concerns about data exploitation and consumer discrimination. The rise of smart advertising has triggered debates on privacy, transparency, and ethical use of personal information.
**Finding the balance between technology and security**
Concerns about data security are not new. Germany introduced the right to self-determination of personal data as early as 1983, and in 2014, the concept of the “right to be forgotten†was formally proposed. The EU’s General Data Protection Regulation (GDPR), set to take effect in 2018, further strengthens these protections.
Judicial practices have also evolved. Google faced legal challenges over the “right to be forgotten,†leading to landmark rulings that emphasize individual privacy rights.
On the technical front, researchers are developing countermeasures against facial recognition, such as anti-face recognition glasses and makeup techniques designed to confuse algorithms. These efforts highlight the ongoing battle between innovation and privacy.
Ultimately, data privacy is a double-edged sword—it brings both risks and opportunities. Proper protection can lead to better services, reduced costs, and enhanced user experiences. But the key lies in finding the right balance.
As technology continues to advance, so must our approach to data security. Solving this complex issue requires collaboration across disciplines—technology, law, policy, and ethics—to ensure that progress doesn’t come at the cost of personal freedom.